Webhooks make it super easy to build on top of Qiscus chat SDK. They are user-defined callbacks. They are triggered by events. When the event occurs, the webhook will make a http(s) call to the URI it’s configured to.
On Post Message
Webhooks on post message being triggered either from Qiscus Chat SDK client side or from Server API whenever send a message.
On Client Post Comment, triggered when client side send a messageOn Rest Post Comment, triggered when server API send a message
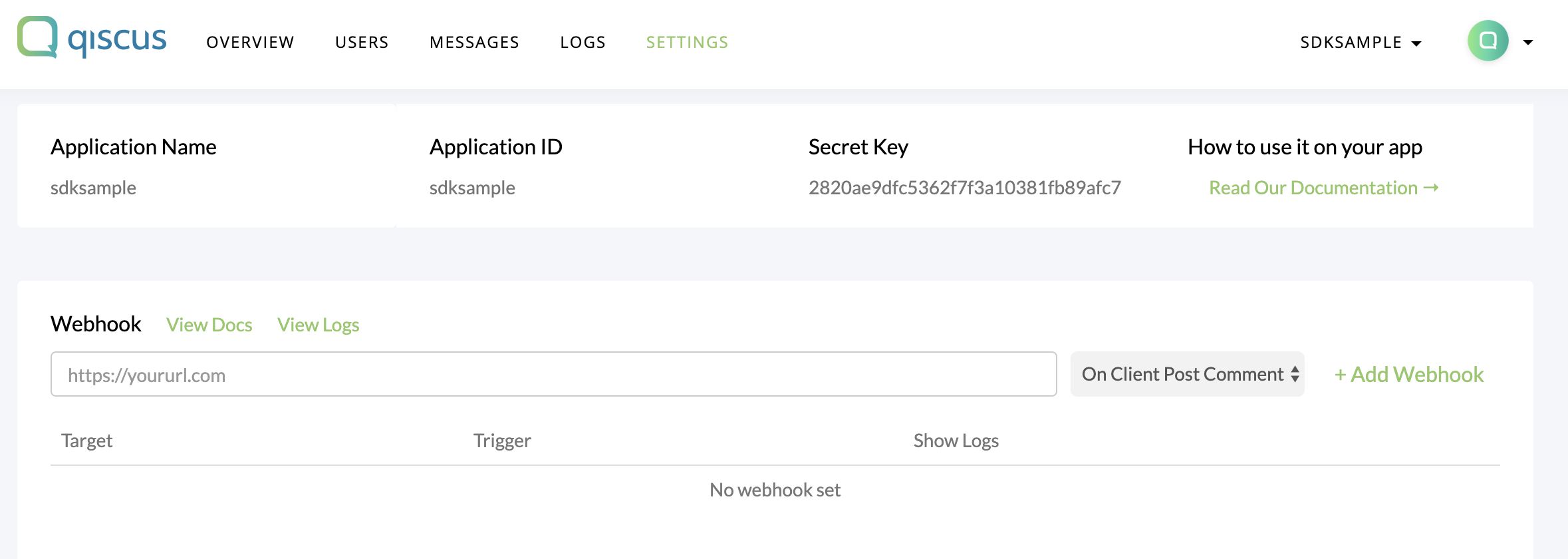
You can setup webhook in Qiscus Dashboard. Go to Setting then add your webhook.
After succeed setup webhook, and the event being triggered, you will receive payload below:
Payload :
{ "type": "post_comment_mobile", // either type "post_comment_mobile" if from client side or "post_comment_rest" if from REST API "payload": { "from": { "id": 1, "email": "[email protected]", "name": "User1", }, "room": { "id": 1, "topic_id": 1, "type": "group", // can also be single "name": "ini grup", // deprecated for the participants data "participants": [ { "id": 1, "email": "[email protected]", "username": "User1", "avatar_url": "http://avatar1.jpg" }, { "id": 2, "email": "[email protected]", "username": "User2", "avatar_url": "http://avatar2.jpg" } ] }, "message": { "type": "text", "text": "ini pesan", "payload": { // comment type specific payload } } }}If the chat room type is a channel (is_public_channel = true) then webhook only sends payload consist of user, room, message, not include the participants
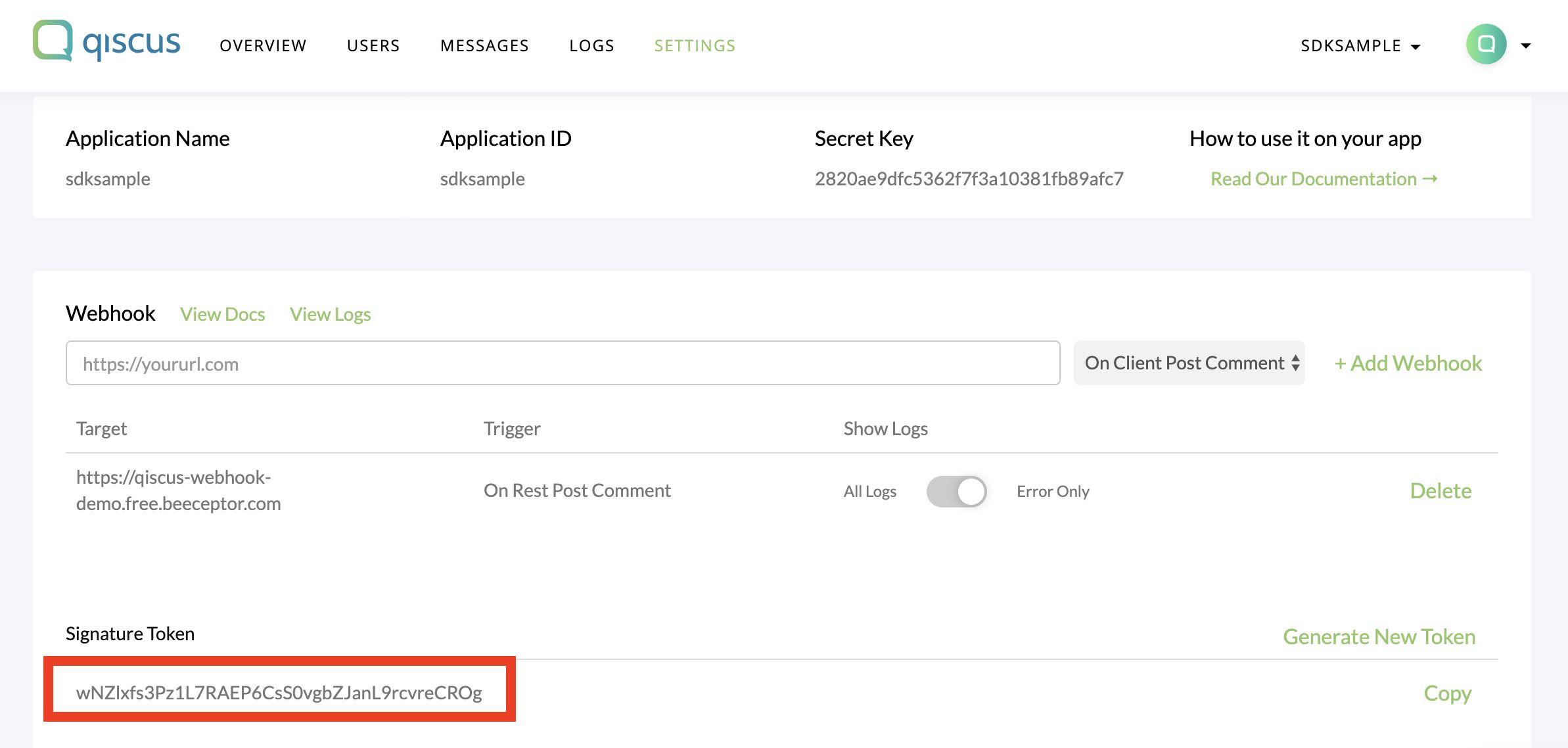
Signature token
For security reasons, you probably want to limit requests to those coming from Qiscus. You can do by generating webhook signature token.
When your signature token is generated, Qiscus uses it to create a hash signature with each payload.
This hash signature is passed along with each request in the headers as QISCUS-SDK-SIGNATURE. The signature token is generated by SHA256. To ensure request from Qiscus, you need to validate that the hash from Qiscus matches with QISCUS-SDK-SIGNATURE. Here example on how to validate the signature token:
package mainimport ( "crypto/hmac" "crypto/sha256" "encoding/hex")func main() { token := "YOUR_SIGNATURE_TOKEN" payload := `{"payload":{"from":{"avatar_url":"https://image.url/image.jpeg","email":"[email protected]","id":140220,"id_str":"140220","name":"Qiscus Demo"},...},...}` // Create a new HMAC by defining the hash type and the key (as byte array) h := hmac.New(sha256.New, []byte(token)) // Write Data to it h.Write([]byte(payload)) // Get result and encode as hexadecimal string signature := hex.EncodeToString(h.Sum(nil)) // Do a check or validation, whether the signature comparison you have made is the same as the qiscus-sdk-signature request header that sent by Qiscus if signature == "qiscus-sdk-signature" { ... }}